

Internet Security and Firewalls deals with issues of protecting one's internal network from the Internet. Although most companies are concerned about exposure to the Internet, many times internal users and employees can pose a greater security threat. Individuals working within the company can compromise a company's financial or technical standing by having unrestricted access to vital company information such as proprietary data and payroll information.
Internet security deals with identifying a security policy for a company's network. A policy would consist of which users on the Internet or internal network should have or not have access.
As the Internet becomes more popular and users become more widespread, company's will find that many employees will want to work from remote sites. However, if a security policy is not in place at a company's site, not only will the employee have access to internal information from the Internet, but, so will anyone else who is connected to the Internet. Currently, anyone having a personal computer with a modem will have access to the Internet and ultimately to all machines on the Internet.
For these reasons, it is imperative that all companies planning to connect to the Internet implement a security policy and install a Firewall within their network. The Firewall should be implemented as a gateway to and from the Internet and the company network.
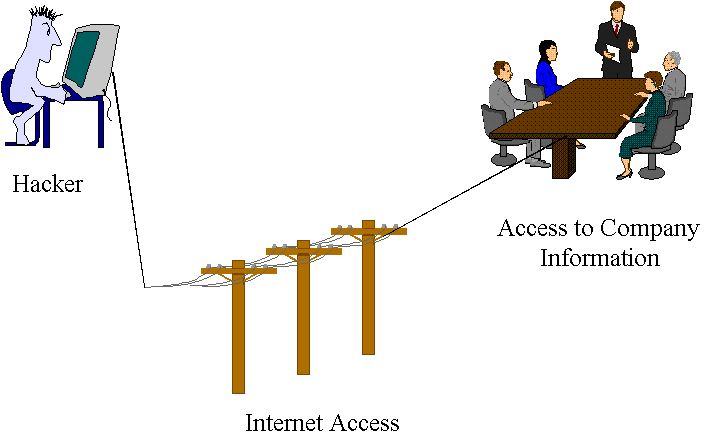
The figure below shows an example where an Internet hacker can tap into vital company information via the Internet.
 |
Whenever a company or an individual is connected to the Internet, the individual is exposed to threats. Below are some of the threats that connecting to the Internet without proper security can be:
The above items are by no means complete. Real life experiences by companies that have experienced a vandal hacker could expand on this list considerably.
Understanding the security risks involved in connecting to the Internet is the first step in developing a security policy and securing a company's network. Once a security policy has been identified, an implementation of a Firewall would be the next logical choice.
The company's security policy should dictate the following:
When identifying a perimeter security rule set, all access paths leading into the network should be screened by the Firewall. The Firewall should have a combination of Internet Packet (IP) filtering and Proxy services to provide two layers of protection. The IP packet filtering rules are used to allow or disallow traffic that originates or is destined to a specific IP address. IP packet filtering is the first level of security for screening IP packets entering a company's network.
The next level of Firewall security is proxy services. Proxy services or servers are modified versions of the services that allow connections between computers. Examples of services are the telnet, ftp, http, gopher and sendmail services. By modifying the aforementioned services to be security aware (Proxies), further screening of communication between computers is introduced.
When identifying security in depth, care must be taken to protect access to computers and enforcing strict security policies on each system on the network. Other forms of in depth security policies is to use strong Identification and Authentication features such as Kerberos, SecureID, and S/Key to name a few.
To conclude, Stealth Internet Services, Inc. can provide a complete network solution, implement a security policy for your company and install a commercial Firewall product.
Any company planning to provide their employees with access to the Internet, should first consider implementing a security policy and installing a Firewall. By not following these procedures, a company may be exposed to hostile attacks from the Internet that in the long run will prove to be extremely time consuming, frustrating and costly.
For further information and a list of references, please contact Stealth Internet Services, Inc. at:
Stealth Internet Services, Inc. (R)
10940 NW 12 Court
Plantation, FL 33322
Tele: 954-261-0932
If you have comments or suggestions, email us at
secinfo@stealthnet.com